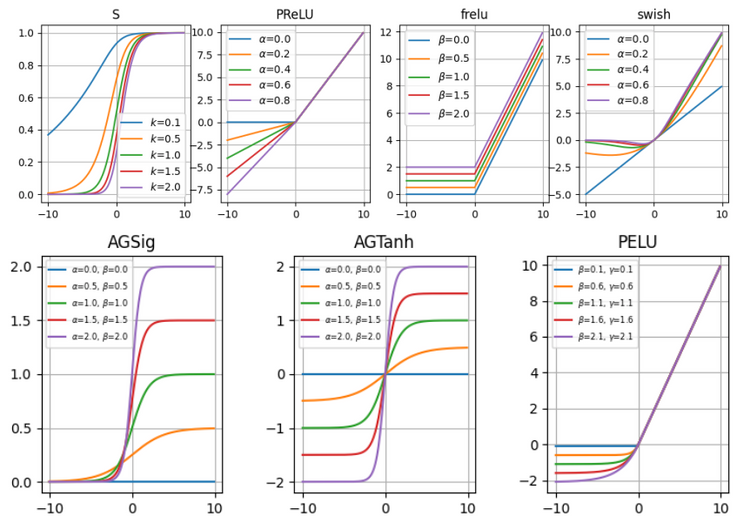
Activation Functions III: Trainable Activation Functions
Introduction The idea of traninable activation functions is not new in the neural networks research field. In recent years, as
Activation Functions II: Rectified-based Activation Functions
Introduction We have given a brief introduction to the basic activation functions in the previous blog. In this post, we
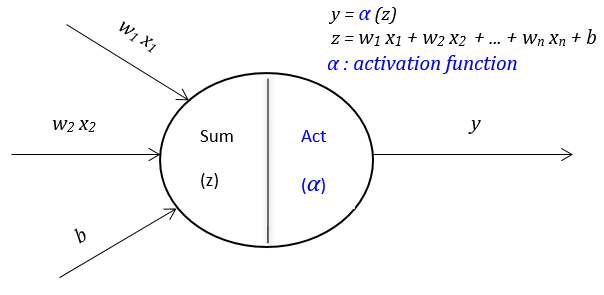
Activation Functions I: Basic AF
Deep learning is actually not a difficult or complicated algorithm. In the whole process of deep learning framework design, the
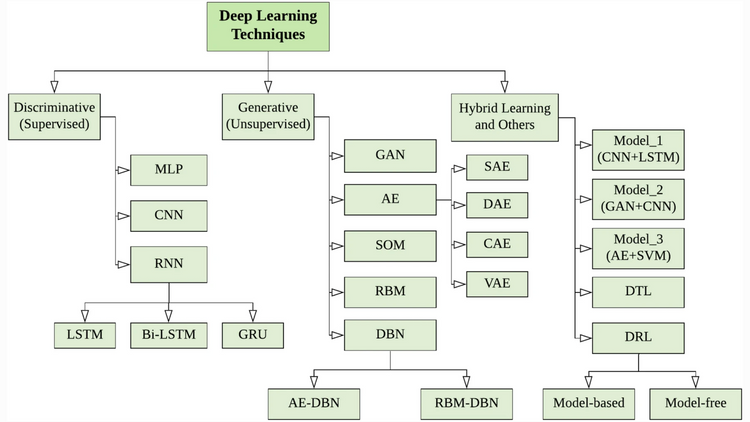
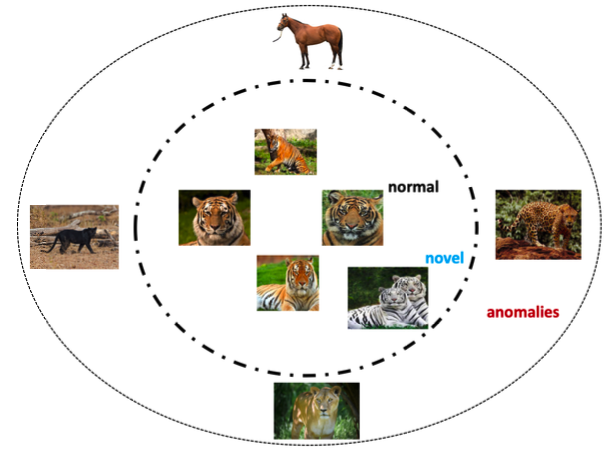
DAD Notes IV: Deep Anomaly Detection Models
In this post, we discuss various Deep Anomaly Detection Models (DAD) classified based on the availability of labels and training
DAD Notes III: Applications of Deep Anomaly Detection
Anomaly detection is applicable in a very large number and variety of domains, such as fraud detection, fault detection, system
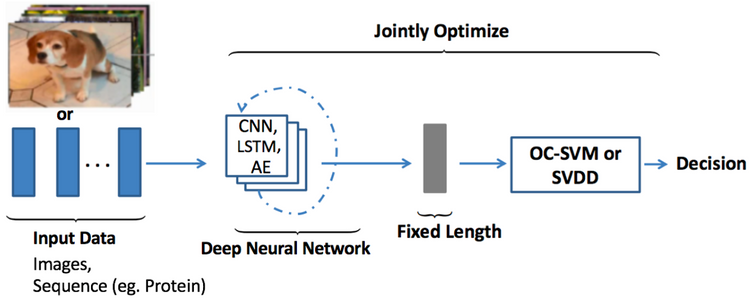
DAD Notes II: Different Aspects of Deep Learning-based Anomaly Detection
Varous deep learning mothods are used to detect anomaly. When we encounter the difficulty to choose an apropriate one, we
DAD Notes I: Introduction to Deep Learning for Anomaly Detection
In data analysis, anomaly detection (also referred to as outlier detection) is generally understood to be the identification of rare